This challenge was part of Facebook CTF . Looking at the challenge tab, the following information is provided:
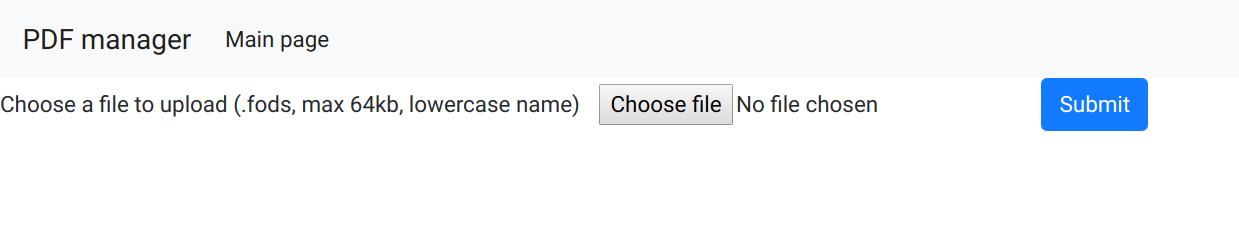
The goal of this challenge is the exploit the PDF conversion service seen below.
Looking at the upload page, a file with .fods extension can be uploaded. This extension corresponds to the OpenDocument Spreadsheet format: OpenDocument_Spreadsheet Fileformat
Lets try to see if we can fake and extension and what result gets uploaded.
1
echo "Hello World" > test.fods
Uploading the above file was successful and a PDF was generated.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
sams@sams-snyk:~$ exiftool 1.pdf
ExifTool Version Number : 10.80
File Name : 1.pdf
Directory : .
File Size : 7.2 kB
File Modification Date/Time : 2019:06:07 23:46:55+01:00
File Access Date/Time : 2019:06:07 23:47:00+01:00
File Inode Change Date/Time : 2019:06:07 23:47:00+01:00
File Permissions : rw-rw-r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Page Count : 1
Language : en-US
Creator : Writer
Producer : LibreOffice 6.0
Create Date : 2019:06:07 22:46:45Z
This shows us that the web application is converting the file to a PDF using LibreOffice 6.0 Calc. By searching exploit-db for relevant vulnerabilities, the following exploit looks probable to work - www.exploit-db.com/exploits/44022
The author also provided a GitHub Repository where the PoC code can be downloaded: poc.fods
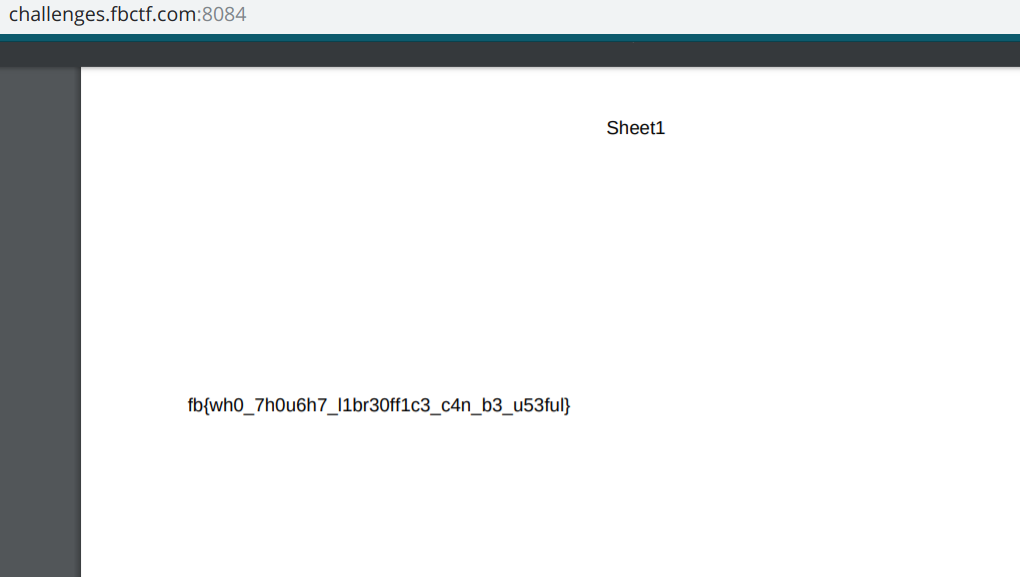
The proof of concept code can be used to read the passwd file within the application’s hosted linux system. Uploading the provided PoC and looking at the created PDF, you can see the passwd file on the system.
Retrieval of the passwd file tells us that the home directory of the libreoffice_admin user is /home/libreoffice_admin. After multiple attempts, the flag was found to be within the follow directory path: home/libreoffice_admin/flag