This challenge was part of Facebook CTF . Looking at the challenge tab, the following information is provided:
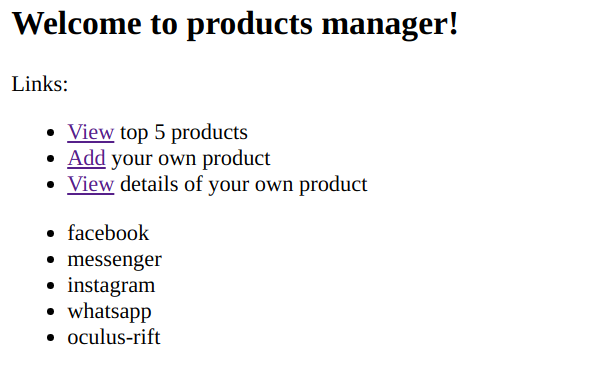
Going to the provided URL, this leads to the following web application where you can add and view your own products.
Going to the view products area shows the top 5 products within the application.
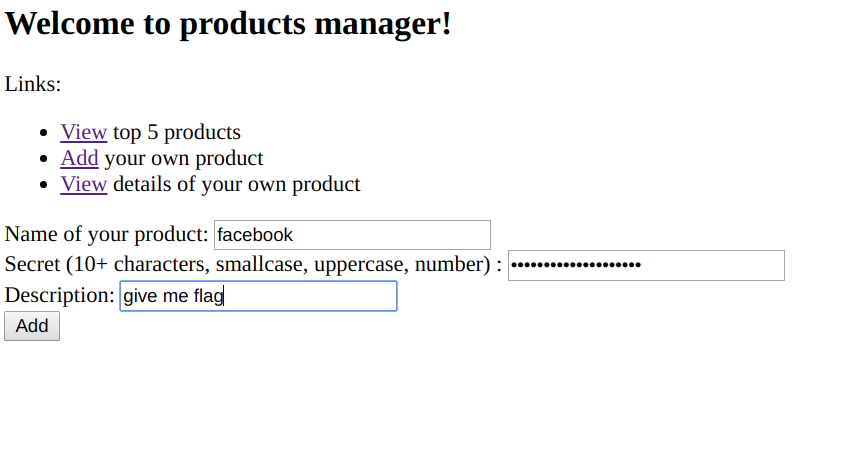
To add a product, a secret needs to be created. After a product is added, this can be viewed and by submitting the product name and the secret. The source code the application is also provided for the challenge.
index.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<?php
require_once("db.php");
$products = get_top_products();
require_once("header.php");
?>
<p>
<ul>
<?php
foreach ($products as $product) {
echo "<li>" . htmlentities($product['name']) . "</li>";
}
?>
</ul>
</p>
<?php require_once("footer.php");
db.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
<?php
/*
CREATE TABLE products (
name char(64),
secret char(64),
description varchar(250)
);
INSERT INTO products VALUES('facebook', sha256(....), 'FLAG_HERE');
INSERT INTO products VALUES('messenger', sha256(....), ....);
INSERT INTO products VALUES('instagram', sha256(....), ....);
INSERT INTO products VALUES('whatsapp', sha256(....), ....);
INSERT INTO products VALUES('oculus-rift', sha256(....), ....);
*/
error_reporting(0);
require_once("config.php"); // DB config
$db = new mysqli($MYSQL_HOST, $MYSQL_USERNAME, $MYSQL_PASSWORD, $MYSQL_DBNAME);
if ($db->connect_error) {
die("Connection failed: " . $db->connect_error);
}
function check_errors($var) {
if ($var === false) {
die("Error. Please contact administrator.");
}
}
function get_top_products() {
global $db;
$statement = $db->prepare(
"SELECT name FROM products LIMIT 5"
);
check_errors($statement);
check_errors($statement->execute());
$res = $statement->get_result();
check_errors($res);
$products = [];
while ( ($product = $res->fetch_assoc()) !== null) {
array_push($products, $product);
}
$statement->close();
return $products;
}
function get_product($name) {
global $db;
$statement = $db->prepare(
"SELECT name, description FROM products WHERE name = ?"
);
check_errors($statement);
$statement->bind_param("s", $name);
check_errors($statement->execute());
$res = $statement->get_result();
check_errors($res);
$product = $res->fetch_assoc();
$statement->close();
return $product;
}
function insert_product($name, $secret, $description) {
global $db;
$statement = $db->prepare(
"INSERT INTO products (name, secret, description) VALUES
(?, ?, ?)"
);
check_errors($statement);
$statement->bind_param("sss", $name, $secret, $description);
check_errors($statement->execute());
$statement->close();
}
function check_name_secret($name, $secret) {
global $db;
$valid = false;
$statement = $db->prepare(
"SELECT name FROM products WHERE name = ? AND secret = ?"
);
check_errors($statement);
$statement->bind_param("ss", $name, $secret);
check_errors($statement->execute());
$res = $statement->get_result();
check_errors($res);
if ($res->fetch_assoc() !== null) {
$valid = true;
}
$statement->close();
return $valid;
}
view.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
<?php
require_once("db.php");
require_once("header.php");
function handle_post() {
global $_POST;
$name = $_POST["name"];
$secret = $_POST["secret"];
if (isset($name) && $name !== ""
&& isset($secret) && $secret !== "") {
if (check_name_secret($name, hash('sha256', $secret)) === false) {
return "Incorrect name or secret, please try again";
}
$product = get_product($name);
echo "<p>Product details:";
echo "<ul><li>" . htmlentities($product['name']) . "</li>";
echo "<li>" . htmlentities($product['description']) . "</li></ul></p>";
}
return null;
}
$error = handle_post();
if ($error !== null) {
echo "<p>Error: " . $error . "</p>";
}
?>
<form action="/view.php" method="POST">
Name: <input type="text" name="name" /><br />
Secret: <input type="password" name="secret" /><br />
<input type="submit" value="View" />
</form>
<?php require_once("footer.php");
add.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
<?php
require_once("db.php");
require_once("header.php");
function validate_secret($secret) {
if (strlen($secret) < 10) {
return false;
}
$has_lowercase = false;
$has_uppercase = false;
$has_number = false;
foreach (str_split($secret) as $ch) {
if (ctype_lower($ch)) {
$has_lowercase = true;
} else if (ctype_upper($ch)) {
$has_uppercase = true;
} else if (is_numeric($ch)) {
$has_number = true;
}
}
return $has_lowercase && $has_uppercase && $has_number;
}
function handle_post() {
global $_POST;
$name = $_POST["name"];
$secret = $_POST["secret"];
$description = $_POST["description"];
if (isset($name) && $name !== ""
&& isset($secret) && $secret !== ""
&& isset($description) && $description !== "") {
if (validate_secret($secret) === false) {
return "Invalid secret, please check requirements";
}
$product = get_product($name);
if ($product !== null) {
return "Product name already exists, please enter again";
}
insert_product($name, hash('sha256', $secret), $description);
echo "<p>Product has been added</p>";
}
return null;
}
$error = handle_post();
if ($error !== null) {
echo "<p>Error: " . $error . "</p>";
}
?>
<form action="/add.php" method="POST">
Name of your product: <input type="text" name="name" /><br />
Secret (10+ characters, smallcase, uppercase, number) : <input type="password" name="secret" /><br />
Description: <input type="text" name="description" /><br />
<input type="submit" value="Add" />
</form>
<?php require_once("footer.php");
Looking at the comments, there is information regarding where the flag is hidden.
1
2
3
4
5
6
7
*
INSERT INTO products VALUES('facebook', sha256(....), 'FLAG_HERE');
INSERT INTO products VALUES('messenger', sha256(....), ....);
INSERT INTO products VALUES('instagram', sha256(....), ....);
INSERT INTO products VALUES('whatsapp', sha256(....), ....);
INSERT INTO products VALUES('oculus-rift', sha256(....), ....);
*/
It seems like the goal of this challenge is to read the description value of the facebook product. This could be possible through SQL injection or brute force of the secret value/field. Looking at the source code, prepared statements seems to be in use.
1
2
3
4
5
$statement = $db->prepare(
"SELECT name FROM products WHERE name = ? AND secret = ?"
);
check_errors($statement);
$statement->bind_param("ss", $name, $secret);
Futhermore, the secret value is also hashed using SHA256 and compared to the one in the database. Looking at the source code, it also not possible to confuse the application by inserting the same product name since checks are in place.
1
2
3
4
$product = get_product($name);
if ($product !== null) {
return "Product name already exists, please enter again";
}
However the following code looks like an entry point
1
2
3
4
5
6
7
8
9
10
11
12
13
14
function get_product($name) {
global $db;
$statement = $db->prepare(
"SELECT name, description FROM products WHERE name = ?"
);
check_errors($statement);
$statement->bind_param("s", $name);
check_errors($statement->execute());
$res = $statement->get_result();
check_errors($res);
$product = $res->fetch_assoc();
$statement->close();
return $product;
}
Tracing the code to where it is being called (see below), the following can be deduced.The check_name_secret function checks if a product exists with the entered name and secret value. However, the get_product function only returns one row from the database by using the name parameter. As such, you could add another product called facebook with a secret and get the application program to return the first already creadted product found with the name facebook.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
function handle_post() {
global $_POST;
$name = $_POST["name"];
$secret = $_POST["secret"];
if (isset($name) && $name !== ""
&& isset($secret) && $secret !== "") {
if (check_name_secret($name, hash('sha256', $secret)) === false) {
return "Incorrect name or secret, please try again";
}
$product = get_product($name);
echo "<p>Product details:";
echo "<ul><li>" . htmlentities($product['name']) . "</li>";
echo "<li>" . htmlentities($product['description']) . "</li></ul></p>";
}
return null;
}
This vulnerability could be exploited using a vulnerability similiar to SQL Truncation Attack. This is due to MySQL comparing values within taking into account trailing spaces. Here we will enter a product with spaces e.g. facebook
The flag can be seen below.