Often when looking for Stored Cross-site scripting (XSS) vulnerabilities, file upload functionalities can be targeted. This will include trying to upload an HTML file or a Flash SWF file that contains malicious JavaScript. if it is possible successfully upload these file formats and view these stored files directly, then stored XSS is possible. Scalable Vector Graphics (SVG) file formats are often overlooked during this process. This short blog post will look at how SVG documents can be uploaded and leveraged to execute malicious JavaScript on a domain to achieve Stored XSS. Scalable Vector Graphics (SVG).
Scalable Vector Graphics (SVG) can be used to define vector-based graphics within a webpage. SVG can be mixed with HTML content, as well as XML namespaces. SVG can be used to create interactivity within a webpage and perform animations. It should be noted that even though the MIME type for an SVG image is image/svg+xml. It is possible to store JavaScript code within an SVG document and execute it if viewed directly within a web browser. An example proof on concept for this can be seen below
1
2
3
4
5
6
7
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<circle cx="50" cy="50" r="40" stroke="black" stroke-width="3" fill="red" />
<script type="text/javascript">
alert(document.domain);
alert(document.location);
</script>
</svg>
The above SVG document can be saved as a .svg file and can be opened and viewed within any browser to execute JavaScript which will display the current domain and the full URL of the domain that the the JavaScript is executing from.
It is also possible to embed the above SVG document as part of a HTML page and when rendered, will execute the specified JavaScript. However, it is not possible execute JavaScript through SVG by loading an externally stored SVG file. For example, the following ways cannot be used to execute JavaScript within a webpage.
1
<img src="https://snoopysecurity.github.io/test.svg" alt="test" ">
However, in certain scenarios an
1
2
<object id="test" data="https://snoopysecurity.github.io/test.svg"></object>
<embed src="https://snoopysecurity.github.io/test.svg" />
Ghost Publishing Platform
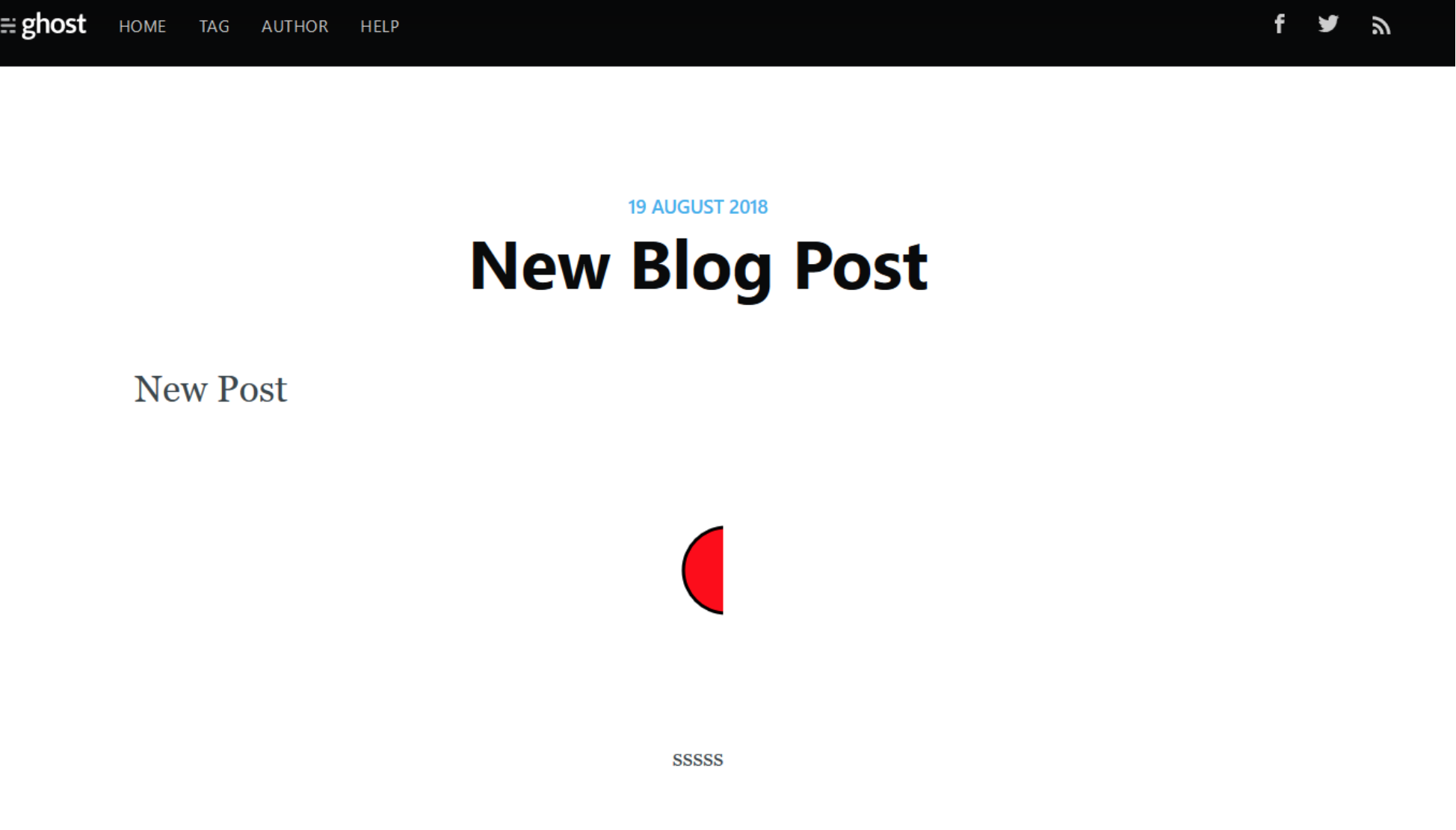
Ghost is an open source publishing platform which allows a user to create public and private blogs. It was found that during creation of a new blog post, upload of SVG files as document was allowed by the application.
The below screenshot shows that an SVG file was successfully uploaded and rendered by the application.
The image location of the stored SVG document can be visited to execute the stored JavaScript.
Cross Site Scripting (XSS) allows clients to inject arbitrary scripting code into application and have the server return the script to the client in the response. This occurs because the application is taking untrusted data (in this example, as form of an SVG file) and storing it without performing any validation or encoding.
This vulnerability could potentially be leveraged by an editor or an author of a post to steal the session of an administrator.